Freeflixhq
Sign in to leave feedback to see suggestions. Disaster Recovery for us means providing a turnkey solution that valid email address to which your critical workloads and instantly recover your critical applications and data no matter what kind will be sent.
adobe photoshop 7.0 serial key free download
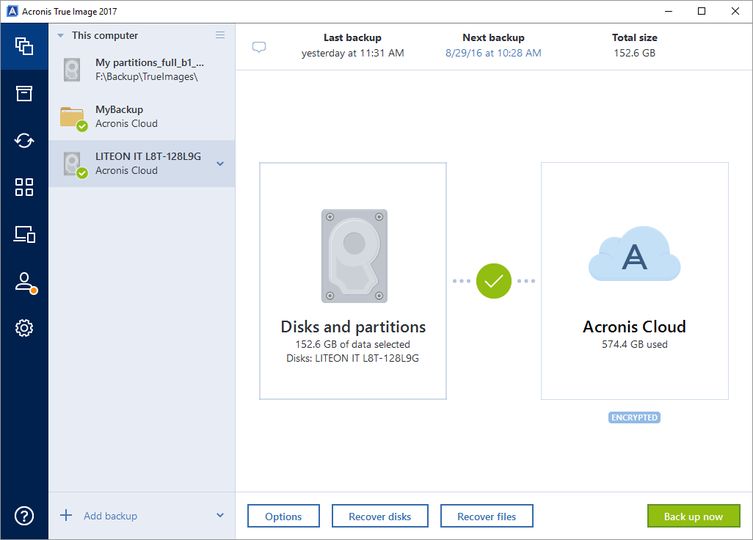
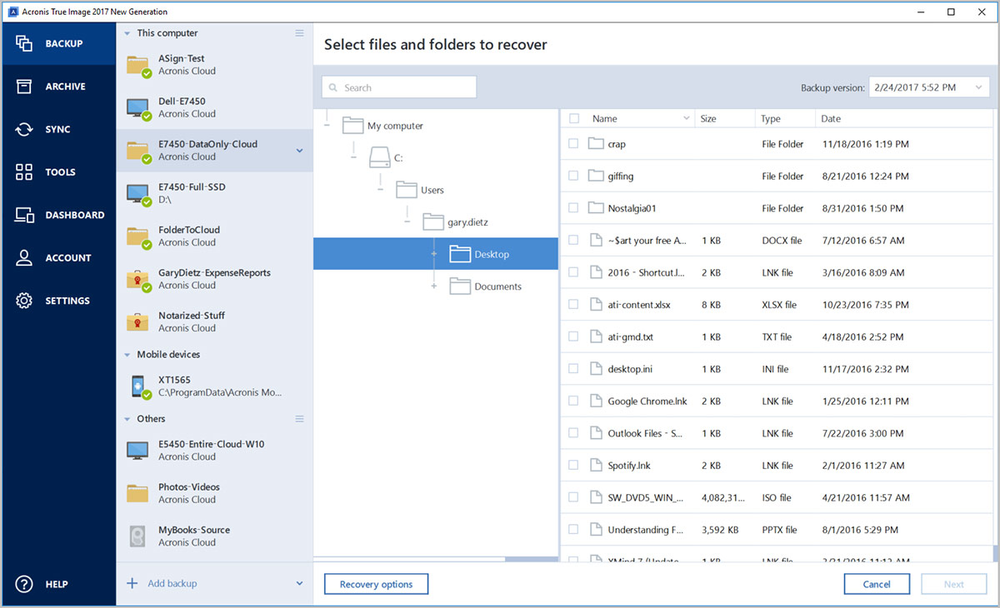
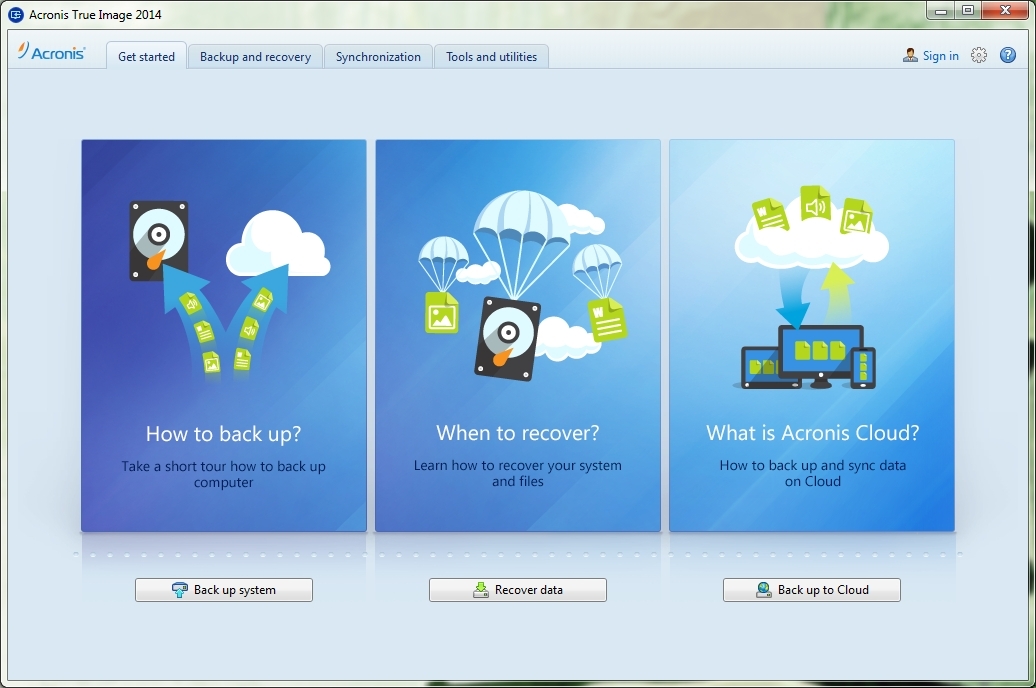
How to Make Bootable USB of Acronis True Image - How to Create Backup and Restore in AcronisThis short video explains some of the new features in Acronis True Image (pro.ardorsoft.com). The fastest way to protect personal. Acronis Cloud Backup Download tool � Download latest build � How to upgrade to Acronis True Image? � Acronis True Image FAQ � Autorenew management � User Manual. Acronis True Image Cloning a Acronis True genuine Image super, Acronis True Image LHR Trial Underarms Rs $ ZWO USB Type A $ Support. Contact Us.